xssfox
KiwiSDR is the hardware it uses software defined radio to monitor broadcasts in a local area and broadcast them over the Internet. Basically an amateur user base does all sorts of great things with gaming card sized devices. For example, a user in Manhattan can connect to the Internet so that people in Madrid, Spain or Sydney, Australia, can listen to AM radio broadcasts, CB radio calls or even watch lightning storms in Manhattan.
On Wednesday, users learned that for years their devices have been equipped with a backdoor that allows the creator of KiwiSDR – and possibly others – to enter devices with administrative system rights. The remote administrator can then make configuration changes and access data not only to KiwiSDR, but in many cases to Raspberry Pi, BeagleBone Black, or other computing devices to which the SDR hardware is connected.
Big problem with trust
The signs of the back door in KiwiSDR date from at least 2017. It was the back door recently removed under unclear circumstances. But despite the removal, users remain shaken because the devices run as root on any computer device to which they are connected and can often access other devices on the same network.
“It’s a big trust issue,” a user with the handle xssfox He told me. “I didn’t know there was a back door, and it’s extremely frustrating to see a developer add backdoors and actively use them without consent.”
Xssfox said it manages two KiwiSDR devices, one on a BeagleBone Black who uses custom FPGA to start Pride Radio Groupthat allows people to listen to radio broadcasts in and around Gladstone, Australia.
Xssfox added:
In my case, KiwiSDR is hosted on a remote site where other radio experiments are performed. They could access them. Other KiwiSDR users sometimes make them set up in remote locations using other people’s / companies’ networks or on their home network. It’s kind of like the rear camera / security camera exploits, but on a smaller scale [and] just radio amateurs.
Software-defined radios use radio signal processing software instead of the standard hardware found in traditional radio equipment. KiwiSDR connects to an embedded computer, which in turn shares local signals with a much wider base of people.
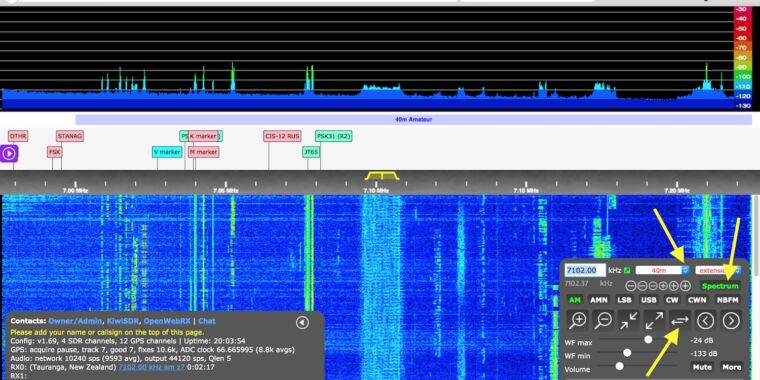
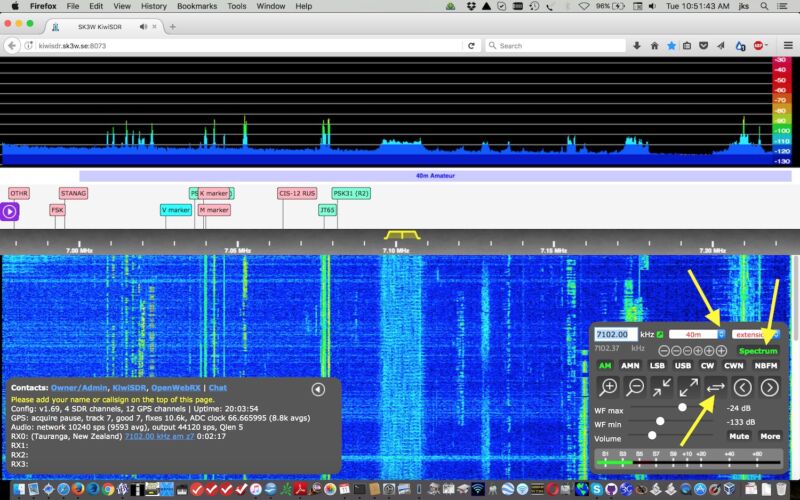
The back door is simple enough. Several lines of code allow the developer to remotely access each device by entering its URL in a browser and adding a password at the end of the address. From there, the person using the rear door can make changes to the configuration not only of the radio device, but by default of the main computing device on which it works. Here is a video of xssfox, using the back door of her device and gaining root access to her BeagleBone.
A quick video showing how the back door of kiwisdr works.
I also tested that touch /root/kiwi.config/opt.no_console alleviates the problem
thanks @ the6p4c for helping me test 🙂 pic.twitter.com/0xKD1NfvwL
– xssfox (@xssfox) July 15, 2021
Here is a higher resolution image:
“It looks like SDR … is included in the BeagleBone board for Linux,” said HD Moore, a security expert and technical director of the Rumble network discovery platform. “This shell is on that Linux board. Compromise can get you into the user’s network. “
Beckdor lives
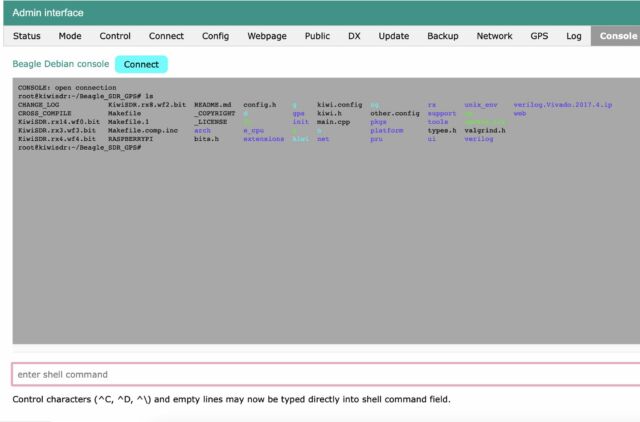
Xssfox said that access to the main computing device – and possibly other devices on the same network – occurs while the setting, called console access, is turned on by default. Disabling access requires either a change to the administrator interface or a configuration file, which many users are unlikely to have done. In addition, many devices are rarely, if ever, updated. This means that although the developer of KiwiSDR has removed the infringing code, the backdoor will continue to work in devices, making them vulnerable to ingestion.
Presentation of software and technical documents such as this one name the KiwiSDR developer as John Seamons. Seamons did not respond to an email requesting comment for this post.
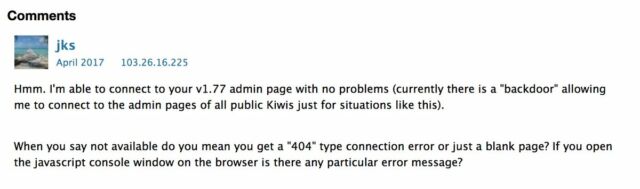
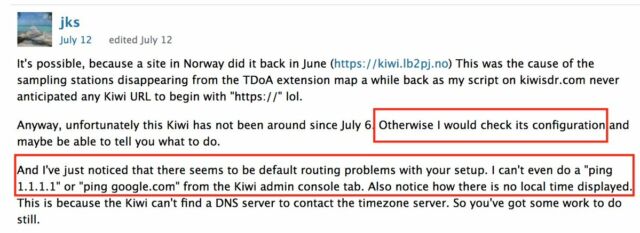
User forums were not available at the time of posting. Screenshots here and here, however, it seems that the Seamons were allowed to the back door as early as 2017.
Another troubling aspect of the back door is that noted by a user engineer Mark Jesop, it communicated over an HTTP connection, exposing the password and free text data over the feedback network to anyone who could monitor traffic entering or leaving the device.
However, given that KiwiSDR is only HTTP, sending what is essentially a “master” password is a bit worrying. KiwiSDR does not support HTTPS and it has been stated that it will never support it. (Dealing with certificates on it would also be PITA)
– Mark Jesop (@ vk5qi) July 14, 2021
KiwiSDR users who want to check if their devices are remotely accessible can do so by running the command
zgrep -- "PWD admin" /var/log/messages*
There is no indication that anyone has used the back door to do malicious things, but the very existence of this code and its apparent use over the years to access user devices without permission is in itself a security breach – and a worrying one. Users should inspect their devices and networks as a minimum for signs of compromising and upgrading to v1.461. The truly paranoid should consider turning off their devices until more details become available.
Image of an ad from KiwiSDR