
The author of a popular software-defined radio project (SDR) has removed the “back door” of radio devices that provide root-level access.
According to the author, the backdoor is present in all versions of KiwiSDR devices for the purposes of remote administration and debugging.
Last night, the author pushed out a “bug fix” in the project’s GitHub aimed at quietly removing this back door, which caused some reaction.
Since then, the original forum posts and the author’s comments with any mention of the “back door” have been removed in the last few hours.
A hard-coded password gives root access to all devices
KiwiSDR is a software-defined radio that can be attached to an embedded computer, such as Seeed BeagleBone Green (BBG).
Available as a standalone board or as a more complete version with BBG, GPS antenna and enclosure.
SDRs are designed to replace radio frequency (RF) communication hardware with software or firmware to perform signal processing activities that typically require hardware devices.
The concept is analogous to software defined network.
Yesterday, Mark Jessop, a radio engineer and radio operator, came across an interesting post in the forum in which the author of KiwiSDR a project recognized for remote access to all radio equipment operating with the software.
An interesting post in the KiwiSDR forums. Does the author of KiwiSDR seem to have remote access to all KiwiSDR? The post has since been modified to remove the last paragraph and the thread is locked: – / https://t.co/cAi5dS7J49 pic.twitter.com/elqSsaUJ65
– Mark Jesop (@ vk5qi) July 14, 2021
Another user, M. excavated a Forum topic for 2017 where the developer of KiwiSDR acknowledged that the rear door does provide them with remote access to all KiwiSDR devices.
Although the entire KiwiSDR forum site is unavailable as of today, an archived copy of the forum post seen by BleepingComputer confirms the content of the tweet:
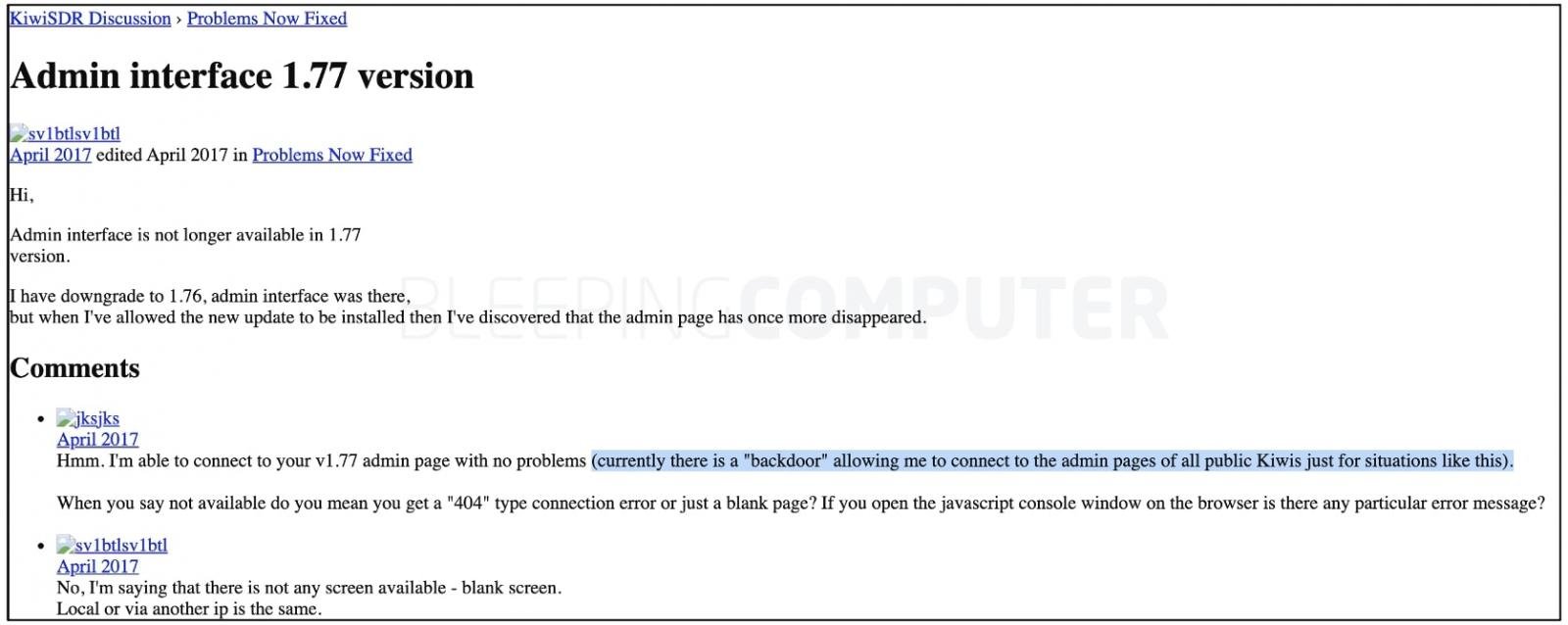
Source: BleepingComputer
In addition, to date, more than 600 KiwiSDR devices are online, with the rear door still present in them, as well as emphasized from Hacker Fantastic.
Although these devices act primarily as radios, it is worth noting that any remote actor who logs in with the encrypted master password gains root access to the device console (based on Linux).
This can allow opponents to explore IoT devices, pick them up, and begin crawling neighboring networks to which radio devices are connected:
“These KiwiSDRs are used to receive high-frequency radios. The back door itself does not give the attacker any special SDR access, only that they can access the device’s console (Linux) and start running on networks,” the ethical hacker said. xssfox said BleepingComputer.
An image of the KiwiSDR admin panel obtained from BleepingComputer shows console-level access with root access (notice #) is possible:
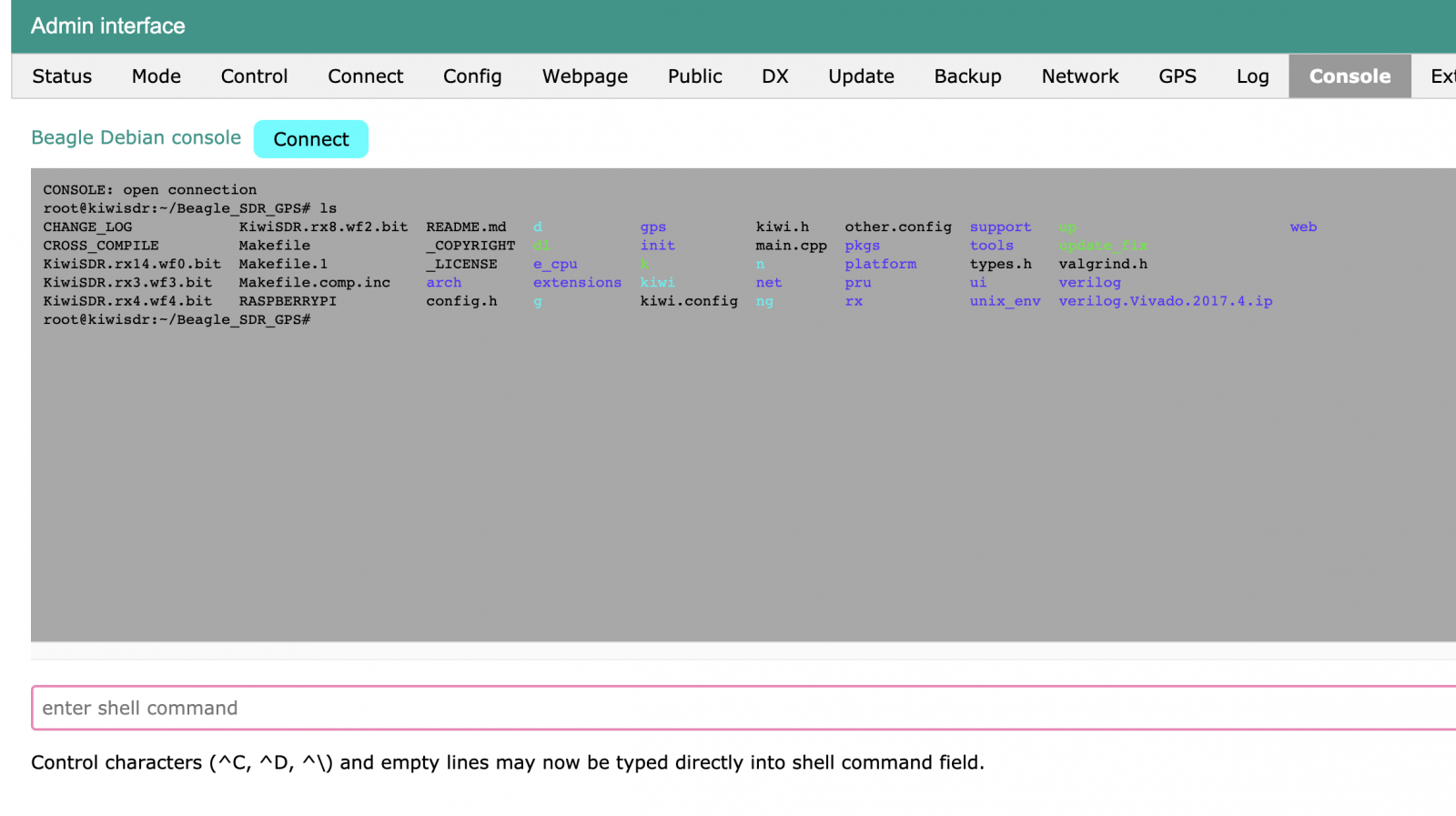
A video created by xssfox demonstrates how the backdoor can be used via a simple HTTP GET request that looks like this:
http://radio-device-domain.example.com:8074/admin?su=kconbyp
Note: The superuser password (kconbyp) shown above is an older password, a SHA256 hash, from which has been present before on KiwiSDR devices. The newer hash (shown below) is different, indicating that “kconbyp” will not work in newer versions of KiwiSDR and that a newer master password is available.
Dev pushes out “error correction” overnight, removing the back door
As can be seen from BleepingComputer, a few hours ago an adjustment was made to KiwiSDR’s GitHub project to remove the rear door.
The update removes a number of administrative features, in particular the code that compares the provided master password with its SHA256 hash:
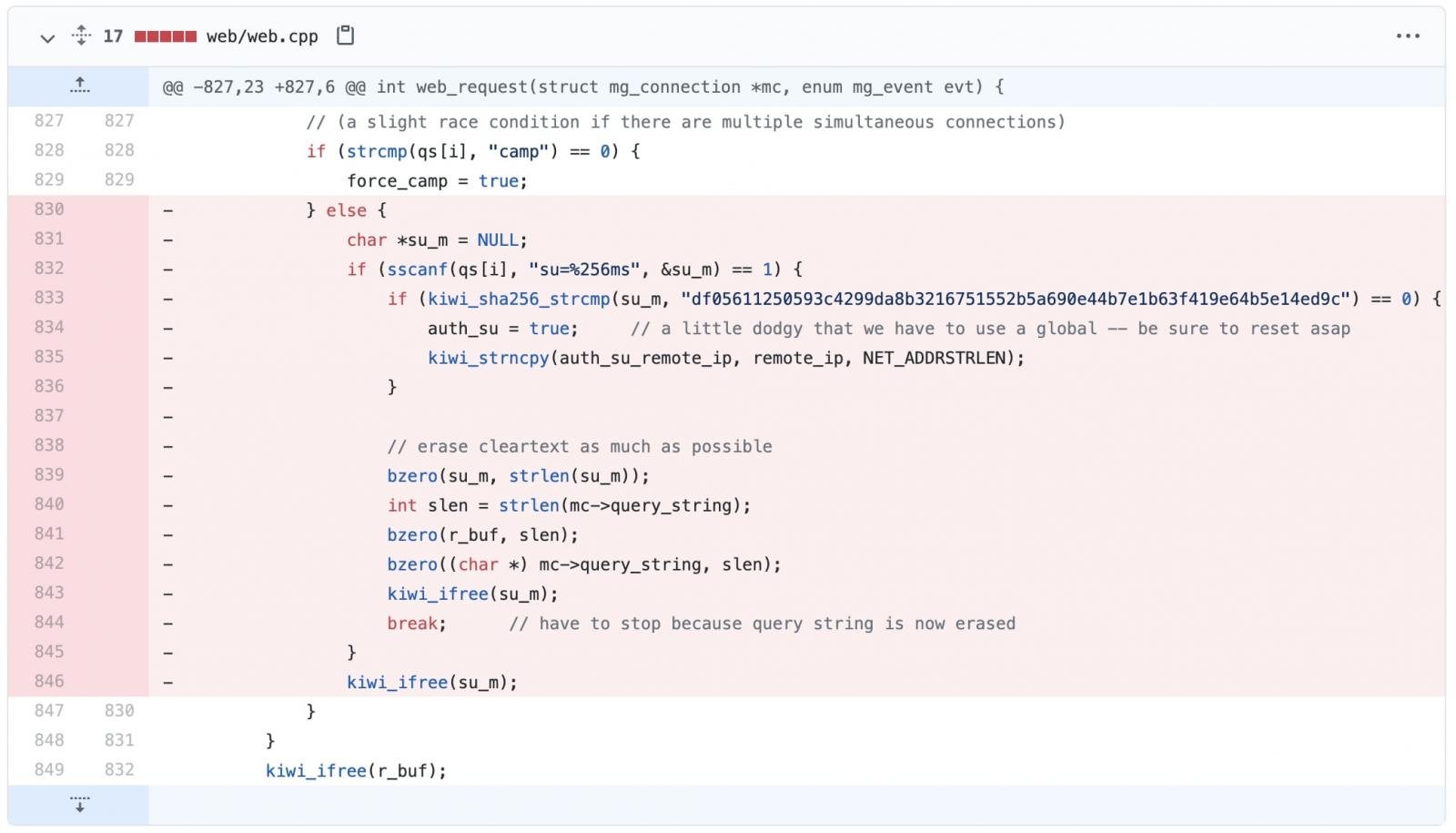
Jessup clarified that there was no indication that the author of the KiwiSDR had misused the rear door, which was introduced with the intention of troubleshooting KiwiSDR devices in good faith.
He also said that the developer of KiwiSDR was extremely responsive in error correction and adding features.
But, like others, the engineer expressed concern that the master password would be transmitted over HTTP, allowing any actor in the “Man in the Middle” (MitM) threat to intercept it and therefore gain remote access to all devices.
However, given that KiwiSDR is only HTTP, sending what is essentially a “master” password is a bit worrying. KiwiSDR does not support HTTPS and it has been stated that it will never support it. (Dealing with certificates on it would also be PITA)
– Mark Jesop (@ vk5qi) July 14, 2021
Some Redditors also said that the rear doors were never OK, whether or not HTTPS was used:
“There’s no way. The back doors are never right. The password was sent clearly because HTTPS is not supported. Eventually someone would use this. Hell, someone might have already used this, and we just don’t know about it. said one of the users in the end.
KiwiSDR users need to upgrade to the latest version v1.461 released today on GitHub which removes the rear door from their radios.

