New vulnerabilities have been discovered in the Fortress S03 Wi-Fi home security system that could be abused by a malicious party to gain unauthorized access to change the behavior of the system, including disarming devices without the victim’s knowledge.
The two unresolved issues tracked under identifiers CVE-2021-39276 (CVSS score: 5.3) and CVE-2021-39277 (CVSS score: 5.7) were discovered and reported by cybersecurity firm Rapid7 in May 2021 for a period of 60 days. to eliminate weaknesses.
The Fortress S03 Wi-Fi Home Security System is a do-it-yourself alarm system that allows users to protect their homes and small businesses from theft, fire, gas leaks and water leaks using Wi-Fi and RFID technology to enter without a key. The company’s security and surveillance systems are used by “thousands of customers and regular customers”, According to to her website.
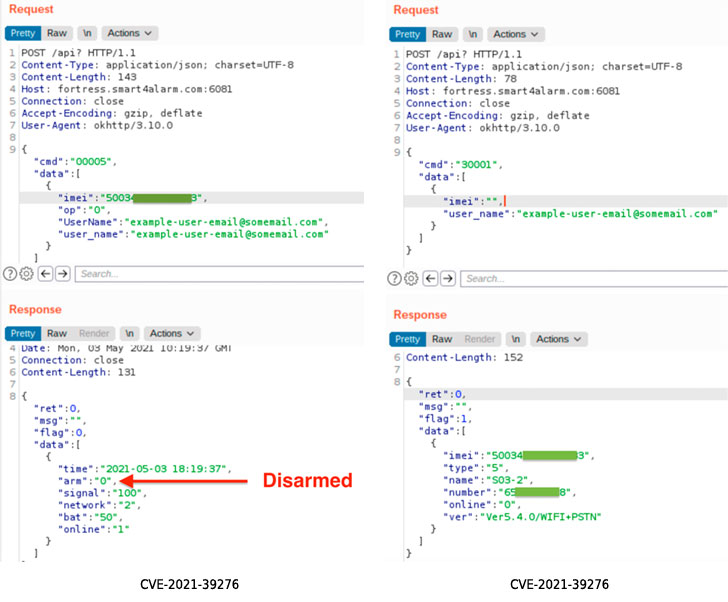
Calling the vulnerabilities “trivially easy to use”, Fast 7 researchers note that CVE-2021-39276 refers to unauthorized access to an API that allows an attacker with a victim’s email address to ask the API to expire the device’s IMEI (International Mobile Equipment Identity) number, which also doubles as a serial number. Armed with the device’s IMEI number and email address, the adversary can make a number of unauthorized changes, such as disabling the alarm system through an unauthorized POST request.
CVE-2021-39277, on the other hand, refers to an RF signal re-attack, where the lack of adequate encryption gives the bad actor the ability to capture the radio frequency command and control communications over the air using software-defined radio (SDR), and to reproduce the transmission to perform specific functions such as “hand” and “operations” to deactivate the target device.
“For CVE-2021-39276, an attacker who knows the email address of a Fortress S03 user can easily deactivate an installed home alarm without that user’s knowledge,” the researchers said in a report shared with The Hacker News.
“CVE-2021-39277 presents similar problems, but requires less prior knowledge of the victim, as the attacker can simply pledge the property and wait for the victim to use the radio-controlled devices within range. The attacker can then play the “deactivate” command again later, without the victim’s knowledge. “
Rapid7 said it notified Fortress Security of the errors on May 13, 2021, only to close the report 11 days later on May 24. We contacted Fortress Security for comment and will update the story if we hear back.
In light of the fact that the problems persist, it is recommended that users configure their alarm systems with a unique, one-time email address to circumvent the exposure of the IMEI number.
“For CVE-2021-39277, it seems that the user can do very little to mitigate the effects of radio frequency reproduction problems, in the absence of a firmware update, to impose cryptographic control on radio frequency signals. Consumers concerned about this exposure , they should avoid using keychains and other radio frequency devices connected to their home security systems, “the researchers said.